|
4G/LTE - Authentication |
||
|
GBA/GAA
GBA stands for Generic Bootstrapping Architecture and GAA stands for Generic Authentication Architecture. This is a kind of mechanism by which a system can share the authentication information (more specifically, the result of authentication) with another system. The authentication information here does not mean 'user id/password' or 'Authentication Key stored in SIM card'. It is more like the information that can be created (processed in a special way) as a result of Authentication that has already been done in a system.
Usually we can say the Authentication mechanism being used in Cellular Network (mostly based on UICC) is much robust and strong comparing to the mechanism being used in other system (e.g, small-scale application service provider). These days, many people are accessing those application service provider through mobile phone and the user has to be authenticated by the service provider via mobile phone. In this case, it would be very good in many ways if those application service can be authenticated by the authentication information provided by the network operator. If this can be doable, those application service provider can utilize those strong authentication mechanism that is provided by Cellular authentication algorithm and Network operator with relatively low cost and at the same time the user experience for the subscriber will be improved as well since they do not need to go through typing in user credentials for authentication. Also, they don't need to remember so many different user IDs and passwords for each service providers. This is the main motivation of GBA.
I think the statement from 3GPP TS 133.220 4 Generic Bootstrapping Architecture is hinting on the motivation of adopting GBA as quoted below.
The 3GPP authentication infrastructure, including the 3GPP Authentication Centre (AuC), the USIM or the ISIM, and the 3GPP AKA protocol run between them, is a very valuable asset of 3GPP operators. It has been recognised that this infrastructure could be leveraged to enable application functions in the network and on the user side to establish shared keys. Therefore, 3GPP can provide the "bootstrapping of application security" to authenticate the subscriber by defining a Generic Bootstrapping Architecture (GBA) based on AKA protocol.
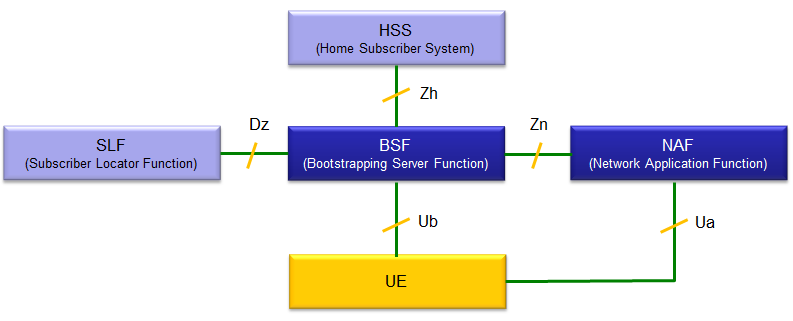
Following is the basic architecture of GBA specified in Figure 4.1 of 3GPP TS 133.220. This is the most basic architecture and there are a couple of more variations of the architecture that you can refer to in the specification. The most important component here is BSF and NSF ('F' means 'Function'. You may take this as a kind of 'Server' or 'Proxy')
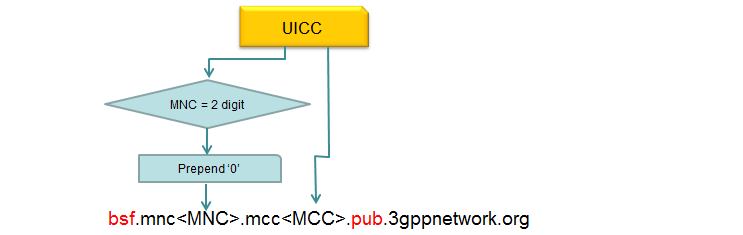
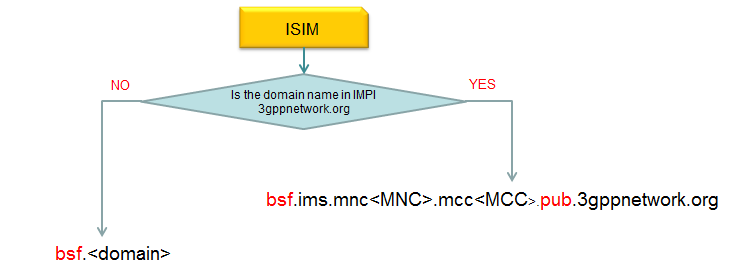
How does UE can figure out BSF address ? According to 3GPP specification (23.003 16.2 BSF address), it can be derived from UICC and ISIM parameters as illustrated below.
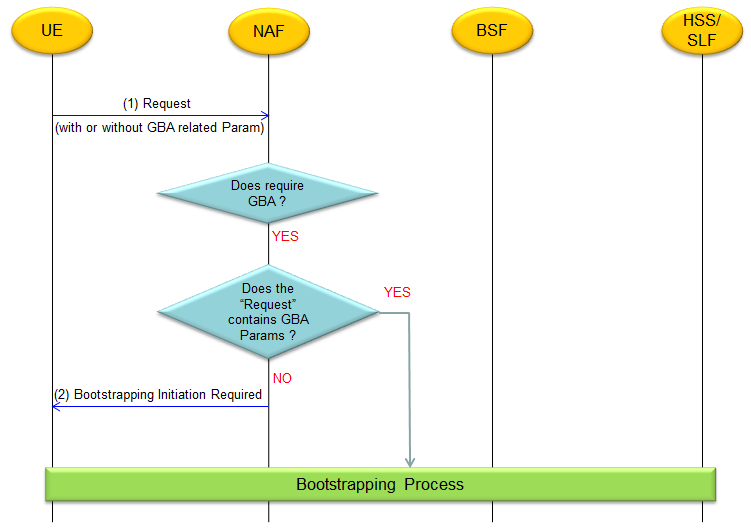
How GBA is initiated (How it gets triggered) ?
How this GBA process get triggered (initiated) ? It is initiated as a result of communication between UE and NSF. ("UE" here would mean a specific Application on UE. Not all application/services would go through this process). Following is overall initiation process, refer to 33.220 4.5.1 for further details.
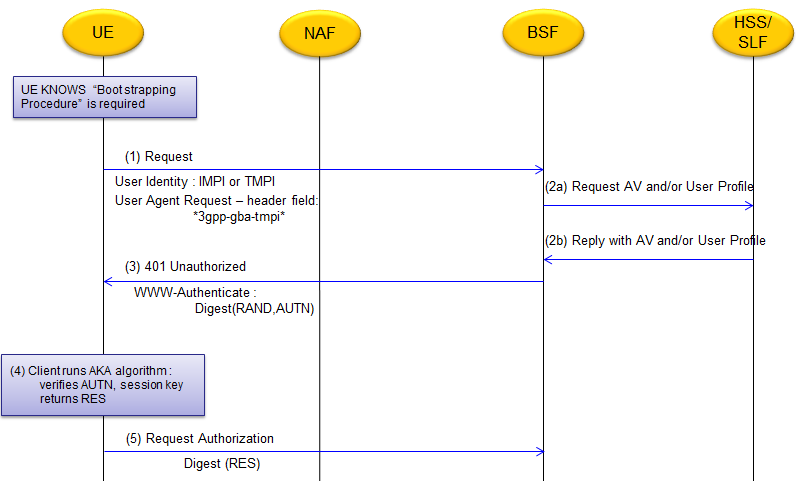
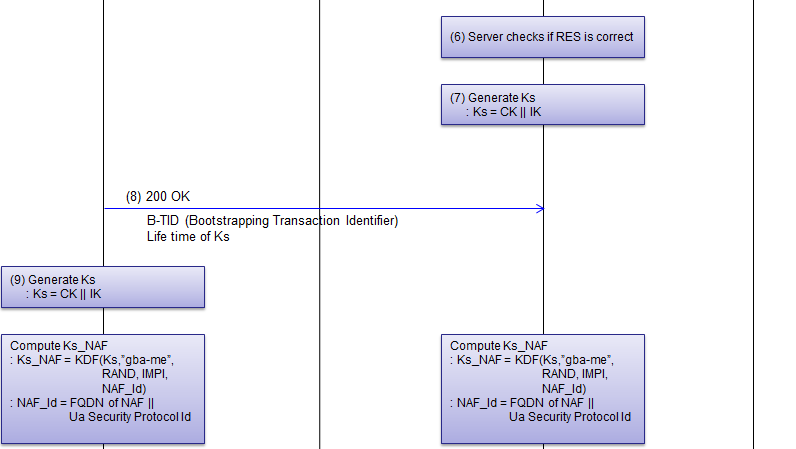
Once GBA process is initiated by various triggers, UE goes through Bootstrapping Procedure. This procedure may vary a little bit depending on cases. In this section, a couple of types of Bootstrapping will be introduced (Most of the details are based on 3GPP 33.220 4.5.2, 4.5.3)
Note : 'AV' in this diagram stands for 'Authentication Vector' and it is defined as AV = RAND||AUTN||XRES||CK||IK
What kind of Keys are used and how they are derivied ?
The most important Keys in GBA process are Ks_int_NAF and Ks_ext_NAF and they are derived as follows.
KDF stands for Key Derivation Function and it is described in 33.220 Annex B (normative): Specification of the key derivation function KDF
|
||