|
|
|||||||||||||||||||||||||||||||||||||||||
|
NAS stands for Non-Access. NAS message is a type of signaling communication exchanged between a mobile device, like a smartphone, and the core network of a mobile operator (e.g., Verizon, T-Mobile). These messages are fundamental for managing the device's state and its services, independent of the specific radio technology (like 4G LTE or 5G NR) used to connect. Think of it like sending a sealed letter. The radio access network (the cell towers) acts as the postal service; it transports the envelope but doesn't know or care about the contents. The NAS message is the letter inside, read only by the sender (your phone) and the final recipient (the core network). This separation allows a single core network to manage devices connected through various radio technologies. Putting it in a little bit formal way, a NAS message refers to a signaling message exchanged between the UE and the core network (especially AMF or SMF) to manage mobility, session, and security procedures. These messages operate at the NAS layer, which is above the radio access layers, and facilitate functions such as registration, authentication, security mode control, and session establishment, ensuring secure and reliable communication without directly involving the radio access network. NAS messages carry critical IEs(Information Element) like UE security capabilities, key set identifiers, and authentication parameters, which may relate across multiple messages to maintain context, integrity, and protection against attacks. Core Functions of NAS MessagesThere are two main categories of NAS messages in terms of core functionality, and together they enable a mobile device to remain connected, exchange data, and do so securely. The first is mobility management, which ensures the network always knows the device’s operational state and general location. This includes procedures such as attaching when the device powers on, detaching when it powers off, updating the network as the device moves, and responding to paging when the network needs to deliver calls or data. The second is session management, which establishes, modifies, and terminates the data connections—known as PDU sessions in 5G -- that form the user’s link to internet and application services. Alongside these two pillars, NAS messages also underpin the network’s security framework by authenticating the device and subscriber, and by generating the encryption keys that protect all subsequent signaling and user traffic.
These messages also play a crucial role in security, handling the authentication of the device and user, and establishing the security keys used to encrypt all subsequent communication, ensuring your calls and data remain private.
Interdependancies Among Messages
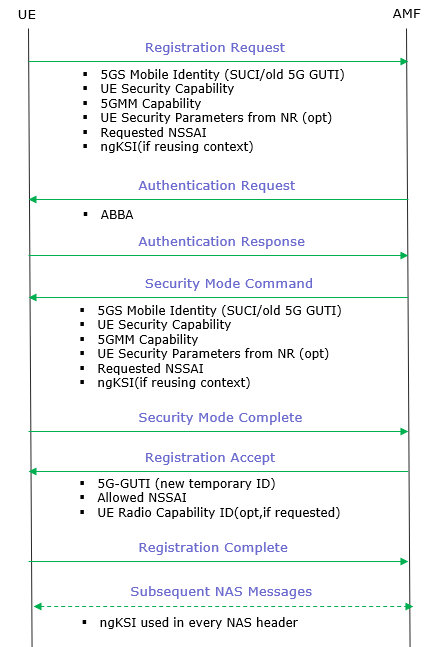
NAS messages are not isolated exchanges but are often interdependent, with specific Information Elements introduced in one message being replayed, referenced, or confirmed in subsequent messages to maintain integrity, consistency, and security throughout the signaling flow. This design ensures that critical parameters such as security capabilities, mobility identities, and network slice requests remain unaltered between different procedural steps, even as messages traverse untrusted access networks. For example, values sent during the initial registration are later echoed in security and acceptance messages, binding earlier declarations to later network decisions and preventing attacks such as capability downgrades, identity spoofing, or mismatched security contexts. These cross-message linkages create a coherent chain of trust from the UE’s first contact with the network to the establishment of secure sessions and ongoing service management. Examples of typical message dependancies and related information elements that interrelates multiple NAS messages are illustrated below
The brief descriptions of the signaling flow in terms of NAS message dependancies are as follows UE Security Capability ↔ Replayed UE Security Capability
5GMM Capability ↔ Replayed 5GMM Capability
UESecurityParametersFromNR ↔ ReplayedUESecurityParametersFromNR
5GS Registration Type / Requested NSSAI ↔ Allowed NSSAI
Requested PDU Session Establishment Parameters ↔ PDU Session Accept
UE Radio Capability ID ↔ UE Radio Capability ID Confirmation
5GS Mobile Identity (SUCI/GUTI) ↔ Assigned 5G-GUTI
ABBA (Authentication and key Binding with Binding Authorization)
ngKSI (NAS key Set Identifier for 5GS)
Summarizing all of these in tabular format in terms of key IE (information elements) flows is following table
|
|||||||||||||||||||||||||||||||||||||||||